Live hosts detection is a very important tool for every penetration tester and ethical hacking. In this tutorial we are going to use Nmap in Kali Linux to scan the network for live hosts. You can use the command ifconfig to determine which IP range you will be scanning for live hosts. We will be using a ping scan on a range of possible live hosts in our network. Nmap will be pinging each host in this range to determine whether the host is live or not. I this tutorial we will be using nmap for scanning and detecting hosts on the network. Needless to say is that there are many tools available for host detection, also for mobile devices. A very popular mobile app for this purpose is Fing Network Scanner. You can download this app in the Apple app store and in the Google Playstore for Android.
Nmap scanning for live hosts
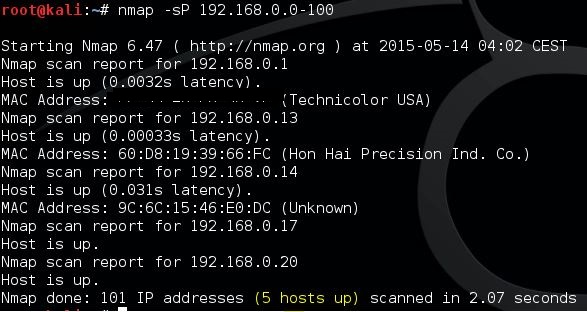
Start a ping scan for live hosts using the following command:
nmap -sP 192.168.0.0-100
Nmap will return a list of all detected hosts:
Add -v to your command to increase the verbosity of the ping scan:
nmap -sP 192.168.0.0-100 -v
This will return all scanned hosts with their status.
Nmap Live Host Scanning video tutorial
Thanks for watching and please subscribe to my YouTube channel :)
Related Nmap Hacking Tutorials
Open Port Scanning and OS Detection with Nmap in Kali Linux
How to enumerate webserver directories with Nmap
Scanning for SMB vulnerabilities using Nmap
Heartbleed SSL bug Scanning using Nmap on Kali Linux


2 Comments
Hi, Is it illegal to scan my own website…will any problem come to me during scanning
Network probing or port scanning tools are only permitted when used in conjunction with a residential home network, or if explicitly authorized by the destination host and/or network. Unauthorized port scanning, for any reason, is strictly prohibited.
Read more on: https://nmap.org/book/legal-issues.html