In the previous parts of the Vulnerability Scanning with OpenVAS 9 tutorials we have covered the installation process and how to run vulnerability scans using OpenVAS and the Greenbone Security Assistant (GSA) web application. In part 3 of Vulnerability Scanning with OpenVAS 9 we will have a look at how to run scans using different scan configurations, review the results and also learn how to run credentialed scans. Finally, we will set up schedules that periodically fire up scanning tasks to automatically scan the network for hosts and vulnerabilities. For demonstration purposes I have booted up several random virtual machines and networked devices in my private lab which will be scanned throughout this tutorial. If you want to follow along with this tutorial, please make sure that you replace all environment specific variables such as IP addresses to match your own environment.
Vulnerability Scanning with OpenVAS 9 Tutorials
- Vulnerability Scanning with OpenVAS 9 part 1: Installation & Setup
- Vulnerability Scanning with OpenVAS 9 part 2: Vulnerability Scanning
- Vulnerability Scanning with OpenVAS 9 part 3: Scanning the Network
- Vulnerability Scanning with OpenVAS 9 part 4: Custom scan configurations
Running customized vulnerability scans
In the previous part of Vulnerability Scanning with OpenVAS 9 we’ve learned how to run a vulnerability scan against a single target on the network. In this part we will configure a host list and run scans periodically using a schedule.
Creating a Target list for host discovery
Before we can run a scheduled task on specific hosts or subnets we have to create a list of targets. To do this, click the ‘Targets’ menu item from the ‘Configuration’ menu and click the blue icon in the top left corner to create a new target:
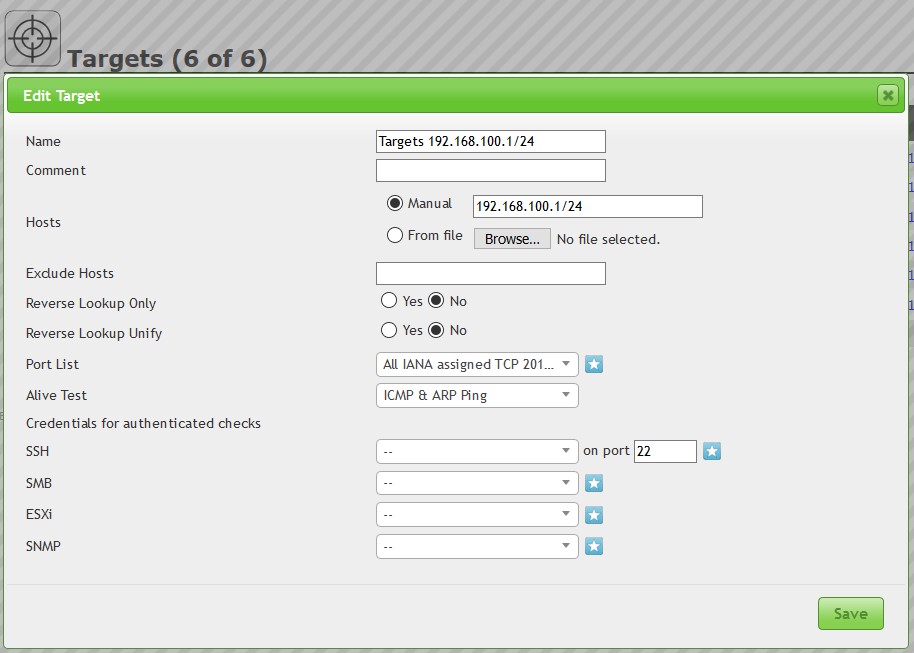
We’ll name the new target ‘Target list 192.168.100.1/24’. In the next section of the new target dialog screen we can specify the target hosts using a few different options. We can either specify a manual host (range), read the hosts from a file or create a target list from the host assets. The last option is greyed out as we currently have no hosts assets in our inventory. When you have to scan multiple subnets using a single target list it’s easier to read the hosts from a text file. To do this simply create a text file and separate each target IP or range with a comma on a single line as follows: 192.168.100.0/24,192.168.200.100-110,192.168.300.10
- Single IPv4 address: 192.168.300.10
- IPv4 address range in short format: 192.168.200.100-11
- IPv4 address range in long format: 192.168.200.100-192.168.200.110
- IPv4 address range in CIDR notation: 192.168.100.0/24
For this demonstration we’ll go with the manual option and specify a range of 192.168.100.1/24. This range contains all IP addresses from 192.168.100.1 to 192.168.100.254. Then we have some options to exclude certain hosts, reverse lookups and we can specify the port list and alive test settings. We’ll keep all settings default except the alive test setting which we set to ‘ICMP & ARP Ping’.
Setting up a Host Discovery task
Now that we’ve got our target list set up, let’s run a scan to discover hosts in the subnet we’ve specified earlier in the target list. Go to ‘Scans – > Tasks’ in the top menu and create a new task:
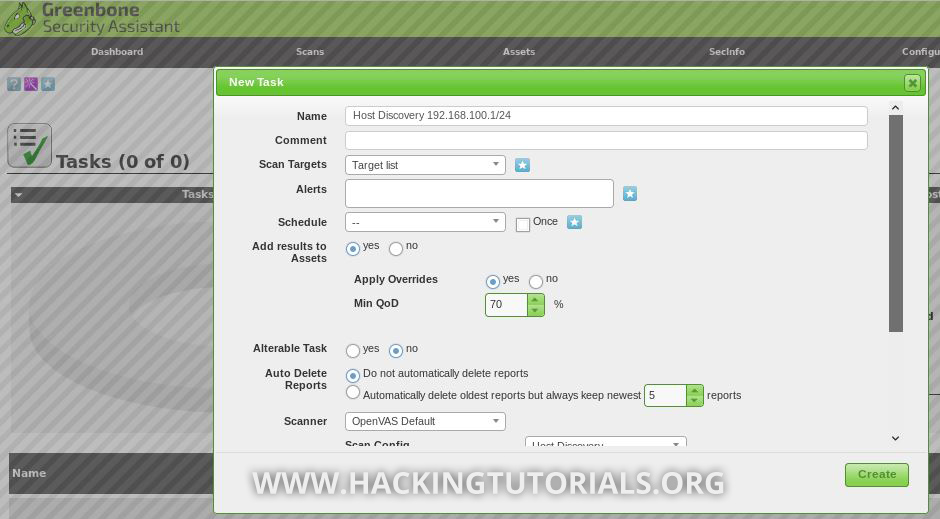
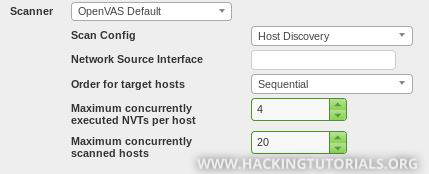
For this task we will set the ‘Scan targets’ option to the newly created target list and we choose to add the results to our assets. Then we will set the ‘Scan config’ to ‘Host Discovery’ and click the ‘Create’ button to create the new scan task:
Next, we run the newly created task by clicking the ‘Run task’ icon:
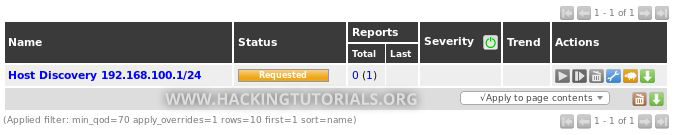
After the host discovery scan is finished we can find the results on the results page (Scans -> Results):
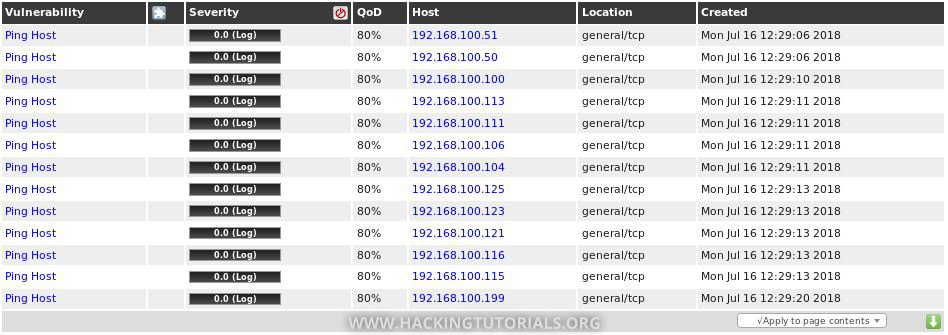
The result list consists of all hosts that were discovered using ICMP or ARP Ping. We can also find the discovered hosts in the assets section of OpenVAS:
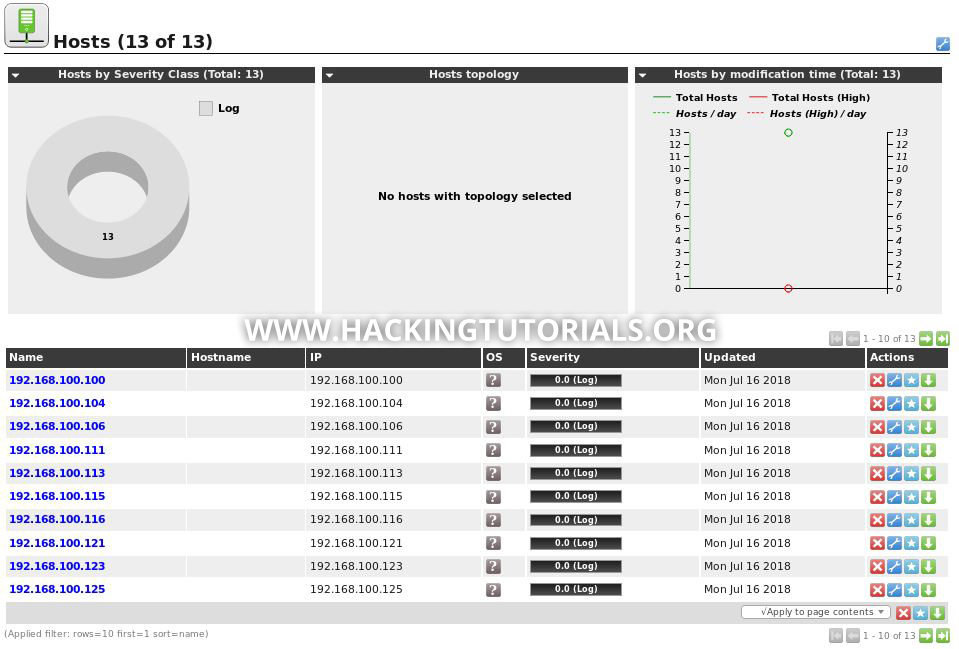
Running a System Discovery scan
We now have an overview of all hosts that responded to our host discovery probes but this only tells us that the host is life. To get some more information about these live hosts we can run a ‘System Discovery’ scan. Before we run this scan let’s have a look at what it exactly does. Go to ‘Configuration -> Scan configs’ and click the System Discovery scan config:
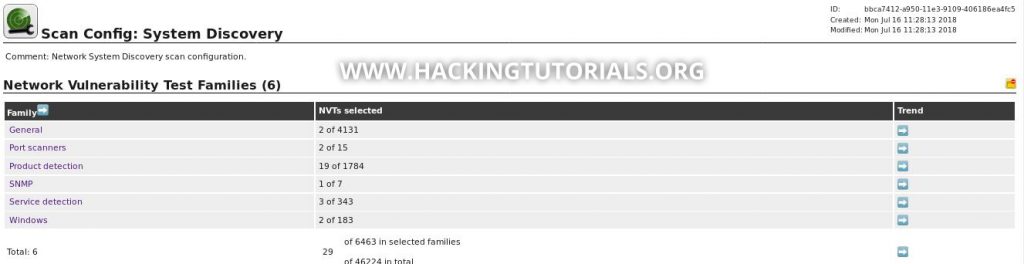
When we click the NVT family entries we can see that the System Discovery scan uses various checks to determine the operating system and to discover SMB servers, printers and various services. Now that we know what this scan does let’s run it on a few targets. From the discovered hosts we’ve selected a few targets and included them in a new custom target list:
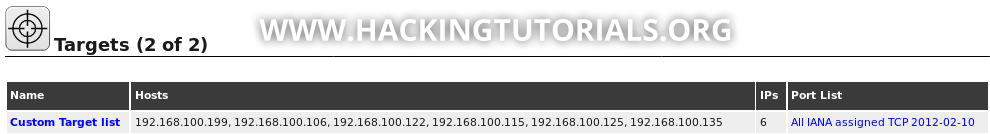
Then we create a new scan task, select the custom target list and finally choose the ‘System Discovery’ scan:
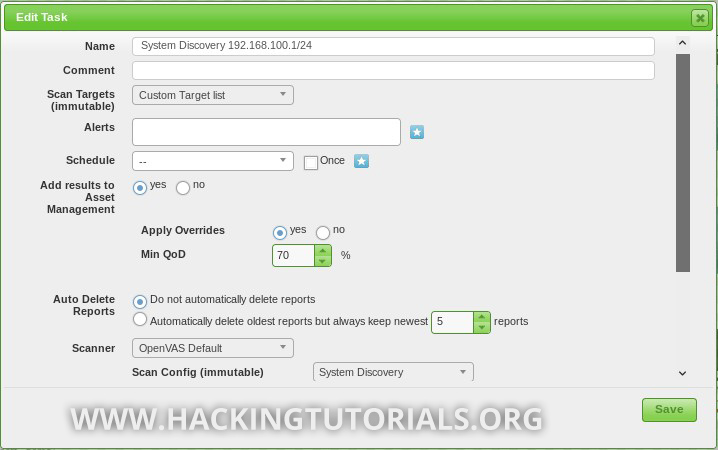
Next, we can execute the task and wait until it is finished.
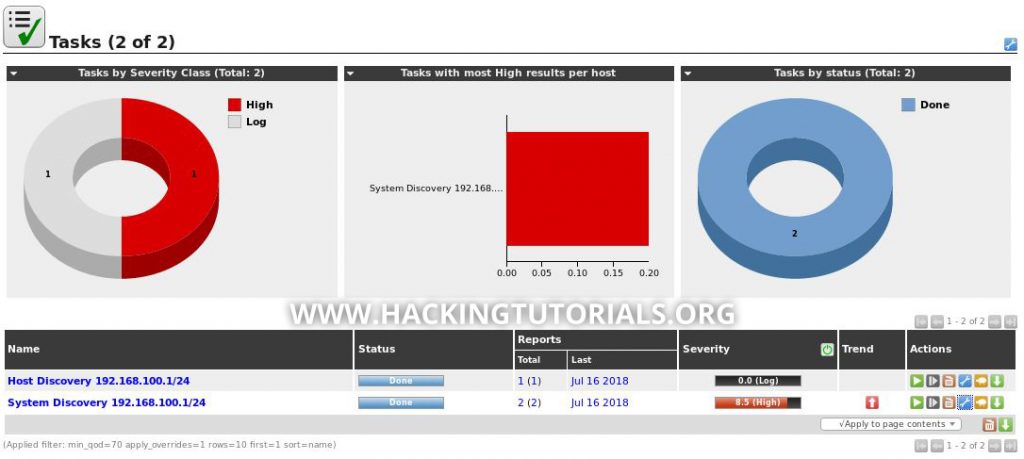
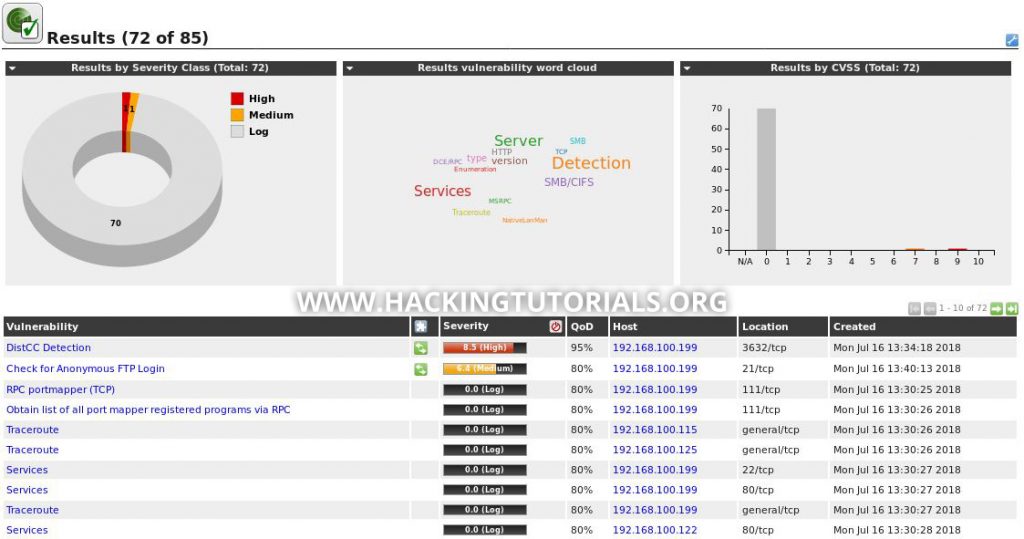
This looks a lot more interesting than the Host Discovery scan, it even found a few severe vulnerabilities with the limited scan configuration. In the scan results we can find that the scan discovered 2 vulnerabilities: DistCC Detection and an FTP server that allows anonymous logins.
Another interesting update took place in the assets section. When we browse to Assets -> Operating Systems we 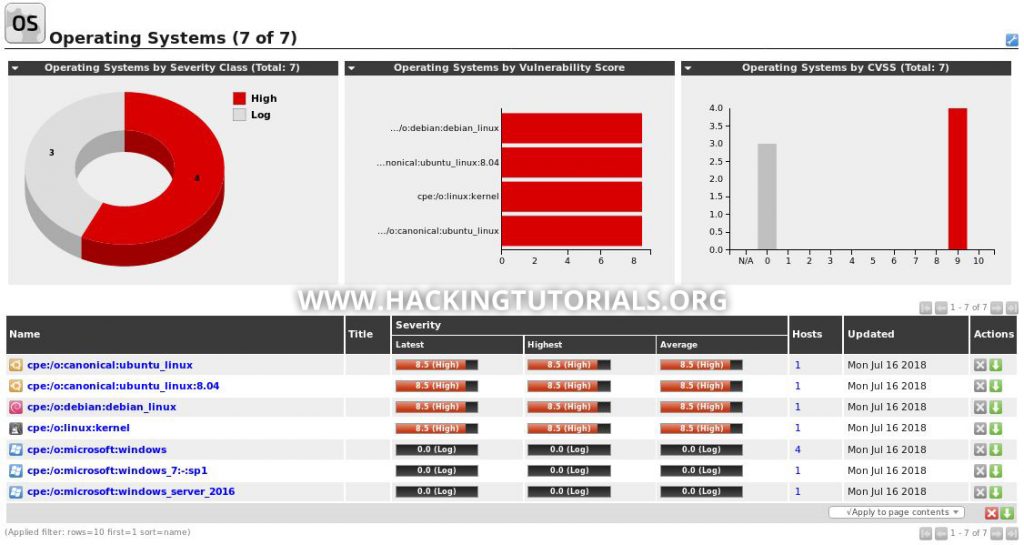
Running a Full & Fast vulnerability scan
Now that we’ve discovered the live hosts on the 192.168.100.1/24 subnet, created a custom target list based on these hosts and ran some scans, let’s run a Full & Fast vulnerability scan. The Full & Fast vulnerability scan is a balanced scan config that is optimized to provide the best results in the least amount of time. This type of scan probes for the most NVTs and uses previously collected information. Let’s set up this scan by creating a new task:
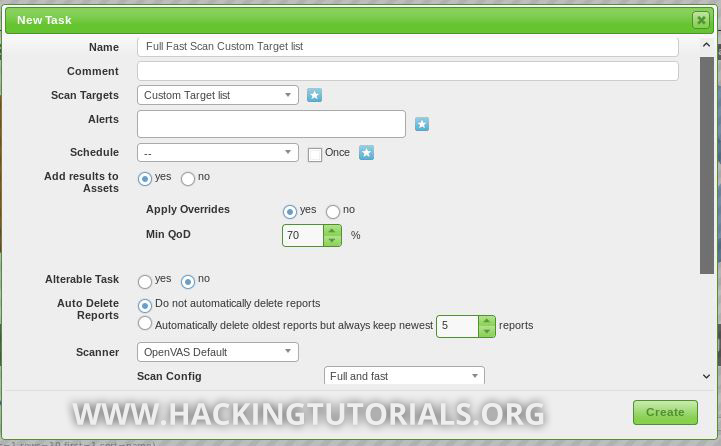
Again, we use the Custom Target list we’ve created earlier and select the Full & Fast scan config. You can also specify how many NVTs and hosts will be scanned simultaneously using the scan config settings. When you’re targeting many hosts with a relatively heavy scan config, please take into account that your machine has enough resources available to effectively perform the scan task. Also take into account that scanning different hosts at once with this type of scan generates a lot of network traffic and might even crash services and hosts. For this demonstration we’ve scanned one host and 20 NVTs at the same time. After a little over 1 hour of scanning, OpenVAS came up with the following results:
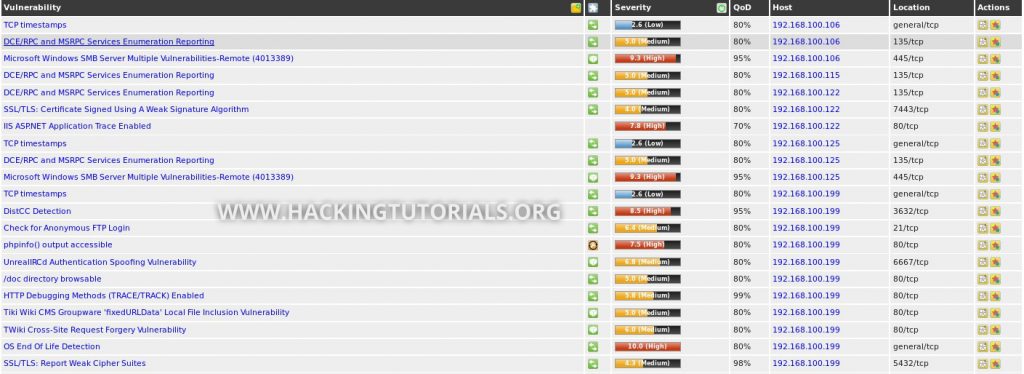
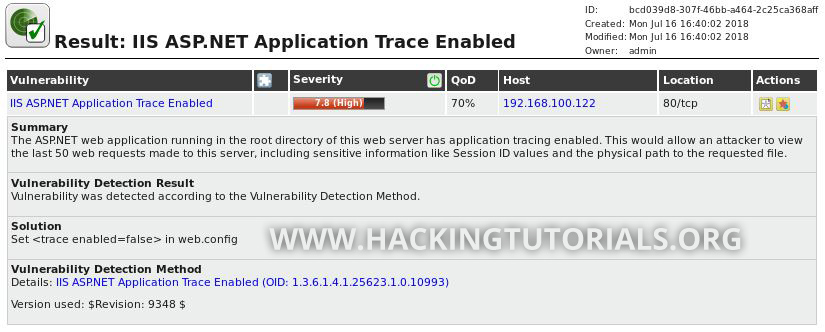
The discovered vulnerabilities range from information disclosure vulnerabilities, such as ‘DCE/RPC and MSRPC Services Enumeration Reporting’ for host 192.168.100.106 to more severe vulnerabilities such as ‘Microsoft Windows SMB Server Multiple Vulnerabilities-Remote (4013389)’ or better known as MS17-010 and EternalBlue. OpenVAS also scan targets for known misconfigurations of which ‘IIS ASP.NET Application Trace Enabled’ is a nice example. A Misconfiguration like enabled application tracing can be abused to allow an attacker to view web requests. These request[FB1] s can include sensitive data such as POST requests with login credentials.
So far, the results are pretty interesting as we’ve found some serious vulnerabilities such as MS17-010. We’ve also found different misconfigurations that allow attackers to retrieve sensitive data from our systems that can be used to access system or provide useful information for later attack stages. At this point I don’t want to go into too much detail about false positives, or even worse false negatives, but scanning tools like OpenVAS can only detect vulnerabilities that it scans for. As I’m scanning my own private lab machines I know there’s a few vulnerabilities/misconfigurations that OpenVAS didn’t pick up and they would go unnoticed without further testing. While OpenVAS did reveal severe vulnerabilities, we cannot rely on scanning results entirely and therefore it is also important to do manual testing in combination with automated scanning. In part 4 of Vulnerability scanning with OpenVAS we will cover false negatives (undetected vulnerabilities) and we’ll have a look at what we can do to avoid this. In the next section we will have a look at how to perform credentialed scans with OpenVAS.
Credentialed vulnerability scans
Until now we’ve only scanned targets for vulnerabilities from the network perspective, such as vulnerable web servers, SMB and FTP servers. We can also supply credentials in the target configuration so that OpenVAS is able to sign in and check for local vulnerabilities such as security issues in kernels and installed software, for example vulnerabilities that allow for privilege escalation. Another way of using credentials is to check a target for default or easy to guess credentials, such as admin/admin. In this case OpenVAS will check the given credentials on a target and report back if they worked correctly. A good use case for this would be creating default credentials when you’re scanning (a range of) Cisco devices. In this case you could add cisco/cisco as username and password or just the username. For this demonstration we will scan Metasploitable 2 and supply admin credentials.
To run credentialed scans on a target we have to create credentials first by going to ‘Configuration -> Credentials’ and click the blue star icon to create a new set of credentials:
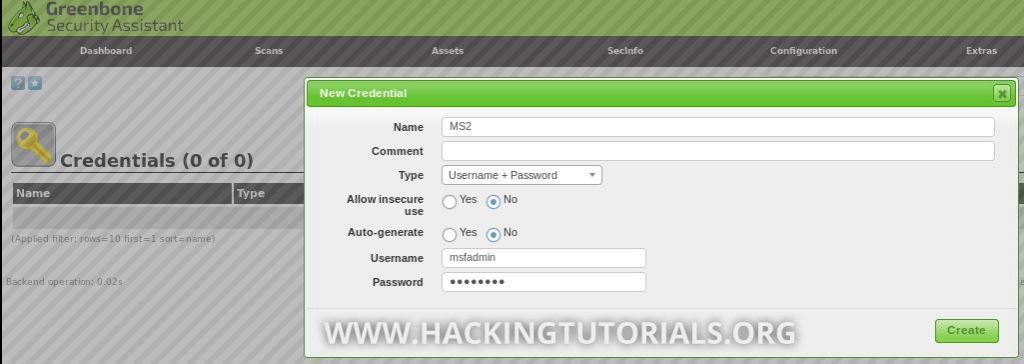
We’ll name it ‘MS2’ and supply the default credentials for Metasploitable 2 (username and password: msfadmin). The next step is to create a new target, enter the target IP address and specify the newly created credentials for SSH access so OpenVAS is able to run authenticated checks:
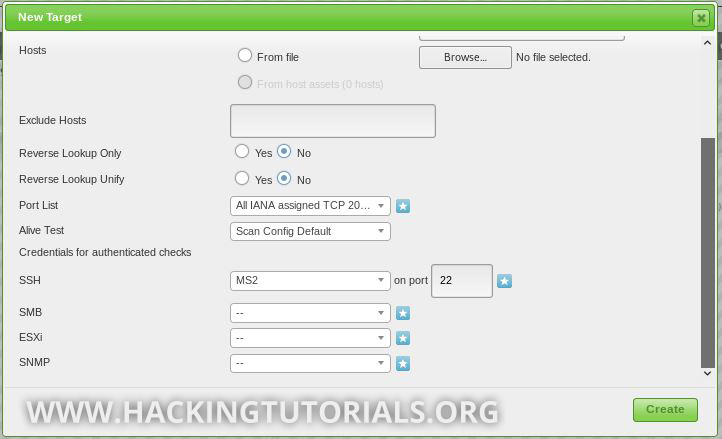
From here you’ll have to create a new scanning task and run it as we already did a few times during this tutorial. Now that we’ve supplied the credentials, local vulnerabilities will be included in the report once the scan is finished.
Scheduling scan tasks
The last topic that we’ll cover in this tutorial is scan task scheduling. Task scheduling is particularly useful when you want to scan a host or network ranges on a regular basis during pre-specified hours. Let’s say we want to run a vulnerability scan on the company network at night when there’s little to no traffic. In this case we can create a daily schedule that runs every day at 11 PM. Let’s have a look at how to do this.
First, we need to create a schedule which we will then assign to a scanning task. To create a schedule, go to Configuration -> Schedules, create a new schedule and specify the desired parameters:
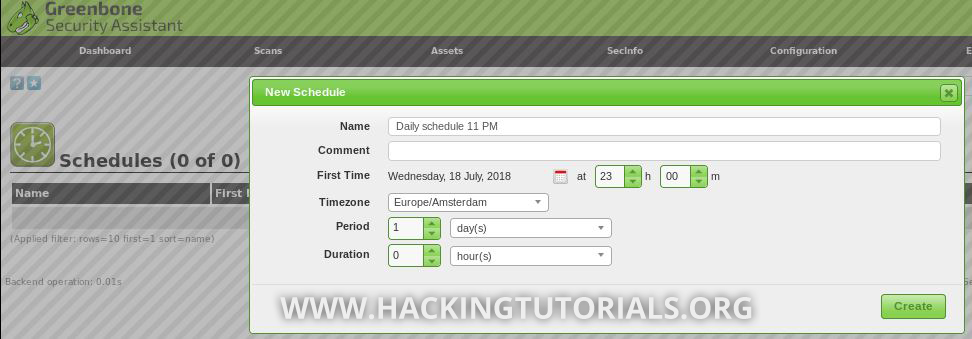
This schedule will run the vulnerability scan every day at 11 PM starting today. The only thing that remains is to create a new scanning task and assign the schedule:
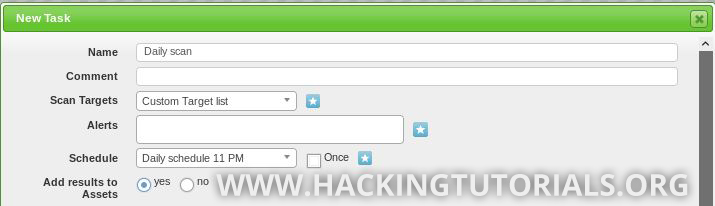
Some final words
By now you should have a good overview of the features and how to perform vulnerability scans with OpenVAS and the Greenbone Security Assistant web application. In this tutorial series we’ve covered the installation process for the local version and the appliance, creating target lists for individual targets and ranges. Then we went on with running different kinds of scans to detect live hosts, discover system information and vulnerabilities. We’ve also covered credentialed scans and scheduling scans to run scan tasks overnight. In the following and final part 4 we will cover custom scan configurations and learn how to configure our own scanning configurations. Custom scan configurations were initially planned for part 3 but as this tutorial has gotten a bit too long already I’ve decided to move this section to part 4. In this part we’ve briefly touched on the subject of false negatives (i.e. undetected vulnerabilities). This is something we will cover too in the next part where we’ll have a look at the limitations of automated scanning tools like OpenVAS and how to avoid them.
Hacking Courses on Udemy
Bug Bounty – An Advanced Guide to Finding Good Bugs
Real World Bug Bounty Techniques

Website Hacking / Penetration Testing & Bug Bounty Hunting
Become a bug bounty hunter! Hack websites & web applications like black hat hackers and secure them like experts.


11 Comments
I’ve installed version 4.2.20, did they take out the scheduling feature? I can’t find it in my install.
Did you install the Virtual Appliance or regular version?
Regular version means installing via apt-get ?
Yes, that’s the one I meant.
I have the virtual appliance on a community feed. It doesn’t include it as well.
The Virtual Appliance.
I am glad for Greenbone. We are not a big shop and don’t want to spend money for big enterprise grade systems like Metasploit. Very happy with the results so far.
Fantastic work
Thank you!
I can’t find the scheduler. I’m using 4.2.24 virtual
I cant find the Schedule. I am using GSM-TRIAL-20.08.8-VMware-Workstation.ova